Kyle Davy and Mike McMeekin
We live in a world in which ever more complex digital technologies are being integrated into our critical infrastructure systems (water, wastewater, electrical, pipelines, and manufacturing). The cyber security threats resulting from this transformation are outpacing the ability of society, and the engineering community, to effectively prevent and manage them.
A new, essential role for the engineering community is emerging — creation and stewardship of cyber-resilient critical infrastructure on behalf of society. Engineering Change Lab – USA’s (ECL) virtual summit on March 19, 2024, explored the magnitude of the threat, the consequences of cyber-attacks, barriers to progress in addressing these threats, and the nature of the “step change” required for the engineering community to fully embrace this leadership role.
Summit provocateur Jonathon Grant of National Grid set the stage for the discussion by quantifying the number of critical infrastructure facilities in the U.S. that are at risk of cyber-attacks.
- 49,680 water systems.
- 14,748 wastewater treatment systems.
- 3,000 electric utilities.
- 292,825 manufacturing facilities.
These facilities are increasingly reliant on digital automation, control systems, and operational technologies. Most have not been designed with cyber risks in mind, and most owner organizations lack cyber expertise. Many engineering organizations working with these systems and advising asset owners also lack cyber expertise. The potential consequences of cyber-attacks on these facilities are serious, including threats to public health, safety, and welfare.
Summit provocateur Mikhail Chester of Arizona State University described the transformation of our critical infrastructure over the last 30 years from “physical systems” to “hybrid physical-cyber systems”. With that has come an accompanying “diffusion of control” over critical infrastructure facilities, with third-party tech organizations now having increasing control over these facilities, further heightening cyber risks. As an example, he cited the influence of Google and Apple on the users of transportation systems, particularly with respect to “maps” apps with traffic information influencing routing choices of individual drivers and ultimately impacting traffic in real time.
What are the barriers to engineering community leadership in addressing cyber security and cyber resilience? Several important barriers surfaced in the discussions at the summit.
- Engineering organizations, both in the design sector and infrastructure owners, are often dismissive of the potential for cyber-attacks.
- We often view cyber issues as somebody else’s problem to deal with – IT or cyber security consultants.
- As summit provocateur Chris Walcutt noted, design engineers do not know the questions that they need to ask to inform their work on behalf of clients and the public.
- Asset owners operate with the assumption that they can count on government intervention and assistance in recovery.
- There is a lack of regulation around cyber issues, which makes it easy to put off addressing issues until it is too late.
- Public policy is even further behind than the engineering community in adapting to these emerging cyber threats. The engineering community can play a critical role building awareness and informing decision makers in the public policy arena.
The leadership needed from the engineering community on behalf of society can only be realized with a shift in mindsets and culture in the engineering community. Cyber resilience needs to be an integral part of our standard of care, elevated to the same level of importance as safety.
Aiding this cultural transformation will be new frameworks such as cyber-informed engineering (CIE), a process developed at the Idaho National Laboratory and demonstrated at the summit by provocateur Andy Bochman. Bochman argues that “engineers will need to accept the new reality (of cyber threats) and develop a new culture that understands cyber-vulnerabilities and employs cyber shields in all new engineering designs.”
The CIE approach centers on identification of critical vulnerabilities, evaluation and prioritization of potential consequences, and the execution of protection and recovery strategies. Strategies developed using CIE often involve non-digital solutions that come from traditional engineering experience and expertise. This framework and thought process can be used to address both existing and new infrastructure.
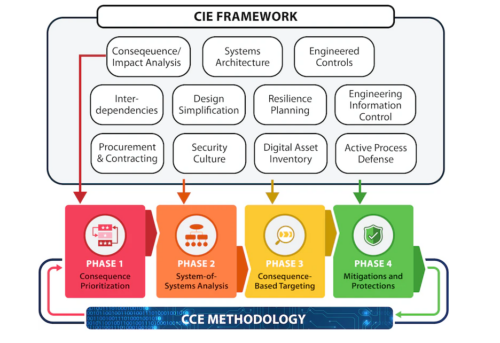
Source: Cyber-Informed Engineering, Idaho National Laboratory
Other key actions from the engineering community include:
- Extend the mindset discussions throughout the critical infrastructure ecosystem, encompassing clients, customers, owners, and users. As Mikhail Chester noted, engineers need to be thinking about this in very different ways and considering a wider range of potential disruptors to preserve public welfare.
- Develop our knowledge and skills in cyber issues through a commitment to learning and training, such as that available through the International Standards Association (ISA) described by summit provocateur Andre Ristaino of ISA.
- Collaborate with organizations in the engineering community who have already committed to leadership in cyber issues such as summit provocateur Chris Walcutt’s organization, Direct Defense.
- Work through our professional organizations to include cyber issues in codes of ethics and manuals of practice.
- Collaborate with universities to ensure that cyber issues are addressed in engineering curriculum.
Cyber security threats rank alongside climate change mitigation and adaptation, extreme weather, natural resource crises, economic disparities, and societal polarization as the most serious risks faced by society now and in the future. Leadership from the engineering community is mandatory if society is to mitigate these risks and maintain a high quality of life for future generations. Hopefully, the learning from ECL’s summit can catalyze a commitment to this leadership on behalf of society.
Provocateur presentations from the summit are available at the Knowledge Hub page of ECL’s website. The full report from the summit is also available.

